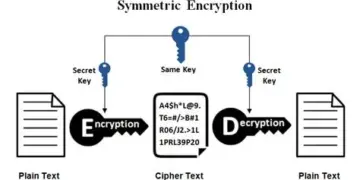
For decades, network security relied on the concept of the “moat-and-castle” model: strong defenses surrounding a corporate network perimeter. Once a user or device successfully authenticated and gained access to the network, they were implicitly trusted to move freely within the internal environment. This model, often called perimeter security, assumed that everything inside the network was safe and everything outside was hostile. However, the rise of cloud computing, remote work, mobile devices, and sophisticated cyber threats—particularly the ability of attackers to gain access via compromised credentials or phishing—rendered the traditional perimeter defense obsolete. Once an attacker breaches the firewall, the implicit trust model allows them to move laterally and access critical data with minimal resistance.
The Zero Trust Architecture (ZTA) emerged as the necessary and profound paradigm shift to address this failure. Zero Trust is a security model centered on the principle of “never trust, always verify.” It mandates that no user, device, application, or network flow is implicitly trusted, regardless of whether it originates inside or outside the traditional network perimeter. Every access request must be rigorously authenticated, authorized, and continuously validated before, during, and after access is granted. This guide provides a comprehensive examination of the Zero Trust model, detailing its core tenants, foundational pillars, and the strategic steps required to implement this crucial framework in the modern enterprise.
1. The Core Principles of Zero Trust Architecture
Zero Trust is not a single product or technology; it is a philosophy built on three foundational pillars recognized by authoritative bodies like the National Institute of Standards and Technology (NIST).
A. All Resources are Accessed Securely
Access to enterprise resources (applications, data, services) is no longer determined by network location. Instead, access is granted through a secure control plane that verifies all components.
-
Decoupled Access: The resource itself must be isolated from the network path used to access it. All traffic must flow through a secure gateway or proxy that enforces policies.
-
Granular Policy Enforcement: Access decisions are based on the specific attributes of the user, the resource being accessed, and the security status of the device.
B. Access is Granted on a Least Privilege Basis
The principle of Least Privilege is central to Zero Trust. Access should be minimal and limited to the scope required for the task at hand.
-
Just-In-Time (JIT) Access: Access permissions are granted for a specific, limited duration and revoked automatically when the session ends or the requirement is met.
-
Need-to-Know: Users are granted access only to the exact resources they need to perform their jobs, minimizing the potential blast radius (the extent of damage) if an account is compromised.
C. Continuous Verification is Required
Trust is never permanent. Even after initial verification, the security posture of the user, device, and connection must be continuously monitored and re-evaluated throughout the entire session.
-
Dynamic Policies: The level of trust is not static. If a device’s security posture degrades during an active session (e.g., if anti-virus protection is disabled or the user logs in from an unusual geographic location), the access policy can dynamically restrict, suspend, or terminate the session immediately.
-
Session Monitoring: All network traffic and resource access attempts must be logged, inspected, and analyzed to detect anomalies or malicious lateral movement.
2. The Seven Foundational Pillars of Zero Trust
Implementing ZTA involves addressing security across the entire IT ecosystem, which can be categorized into several key operational pillars.
A. Identity (The Who)
Identity, encompassing users and non-person entities (applications, services), is the most critical pillar.
-
Strong Authentication: Mandatory Multi-Factor Authentication (MFA) for all identities, regardless of their location, is essential. This prevents credential stuffing and phishing attacks from succeeding.
-
Centralized Identity Provider: All identities should be managed by a single, authoritative Identity Provider (IdP). This streamlines provisioning, de-provisioning, and policy enforcement across all applications.
-
Adaptive Access: Using behavioral analytics and risk engines to determine access. If a user tries to access a sensitive database at 3 AM from a new country, the IdP should require step-up authentication or deny access.
B. Devices (The How)
Devices (laptops, mobile phones, IoT) are the primary entry point for users and must be continuously assessed for security posture.
-
Inventory and Management: All devices accessing enterprise resources must be inventoried and managed through a system (like Mobile Device Management or Endpoint Detection and Response) that can report on their security status.
-
Device Health Check: Access is conditional on the device’s health:
-
Running the latest approved operating system version.
-
Encryption (disk encryption) is enabled.
-
Endpoint security (anti-virus, EDR) is active and up-to-date.
-
-
Contextual Access: Policies must incorporate device posture into the decision. A user on a compliant, corporate laptop may receive full access, while the same user on an unmanaged mobile device may only receive restricted, read-only access.
C. Applications and Workloads (The What)
This pillar focuses on securing the applications and services themselves, whether they are running on VMs, containers, or Serverless functions.
-
Micro-Segmentation: Breaking down the network into tiny segments, often down to the individual application or service level. This limits lateral movement even if an attacker compromises one service.
-
API Security: All application programming interfaces (APIs) must be treated as public-facing, requiring strict authentication and authorization checks for every request.
-
Code Integrity: Implementing continuous vulnerability scanning and static/dynamic application security testing (SAST/DAST) in the development pipeline to ensure code is secure before deployment.
D. Data (The Crown Jewels)
Data protection is the objective of ZTA. Policies must prioritize the data’s inherent sensitivity.
-
Classification and Labeling: Data must be classified (e.g., Public, Internal, Confidential, Highly Restricted) and labeled. Access policies are then tied directly to the data’s classification level.
-
Encryption Everywhere: Data must be encrypted in all states: at rest (in storage and databases), in transit (using TLS/mTLS), and increasingly, in use (using techniques like confidential computing).
-
Data Loss Prevention (DLP): Employing tools to monitor and prevent sensitive data from leaving defined security boundaries.
E. Network (The Transportation)
The network is the substrate that connects the elements, and it must enforce the policy, not define it.
-
Software-Defined Perimeter (SDP): Using technologies to create dynamic, logical access boundaries based on identity and policy, rather than static firewalls and IP addresses.
-
Zero Trust Network Access (ZTNA): This technology replaces the traditional VPN. ZTNA connects a verified user directly to a specific application, making the application invisible on the public network and isolating the user from the rest of the internal network.
F. Visibility and Analytics (The Insight)
Continuous monitoring and analysis are essential for maintaining the Zero Trust security posture.
-
Centralized Logging and SIEM: Collecting all security telemetry (logs from devices, firewalls, applications, and IAM) into a centralized Security Information and Event Management (SIEM) system for real-time analysis and correlation.
-
Threat Detection and Response (XDR): Utilizing advanced Extended Detection and Response (XDR) tools to monitor activity across endpoints, network, email, and cloud environments, looking for deviations from normal behavior.
G. Automation and Orchestration (The Enforcer)
The speed and complexity of the digital environment necessitate automated enforcement and response.
-
Automated Policy Enforcement: Using orchestration platforms to automatically update policies, revoke access, or isolate a device when a security anomaly or degradation in device health is detected.
-
Security Automation and Response (SOAR): Implementing SOAR playbooks to automate the initial steps of incident response (e.g., isolating a compromised identity or terminating a malicious cloud resource), drastically reducing response time.
3. The Policy Engine and Trust Algorithm

The heart of the Zero Trust Architecture is the Policy Decision Point (PDP), also known as the Policy Engine. This component determines whether an access request should be granted.
A. The Policy Enforcement Point (PEP)
The PEP is the gatekeeper—the physical or virtual component (like a firewall, application gateway, or proxy) that enforces the decision made by the Policy Engine.
-
Access Granting: When a user requests access to a resource, the PEP intercepts the request and forwards it to the Policy Engine.
-
Session Management: Once access is granted, the PEP monitors the session for duration, activity, and compliance with the policy.
B. The Trust Algorithm
The Policy Engine calculates a Trust Score for every access request, using a dynamic, multi-attribute approach. The algorithm considers multiple input sources:
-
Identity Attributes: User role, department, history of access, level of MFA used.
-
Device Attributes: Operating system version, patch level, EDR status, physical location (geo-fencing).
-
Environmental Attributes: Time of day, network path, sensitivity of the data being requested, and current organizational risk score.
-
Policy Decision: Based on the calculated Trust Score, the Policy Engine makes a decision: Grant, Deny, Isolate, or Step-Up Authentication.
C. Context is Everything
The decision to grant access is purely contextual. Access is never binary (on/off) but is proportional to the validated trust.
| Trust Score | Action Taken | Example |
| High | Full Access | Employee on corporate laptop, using MFA, accessing non-sensitive app during business hours. |
| Medium | Restricted Access | Employee on personal mobile device, using MFA, accessing email only (no internal drives). |
| Low | Step-Up/Isolate | Employee on corporate laptop, EDR flags malware, access to all resources is immediately denied or isolated to a remediation network segment. |
4. Implementation Strategy: The ZT Roadmap
Migrating to Zero Trust is a phased journey, not a switch-flip. It requires strategic planning and incremental deployment.
A. Focus on Data and Identity First
The most effective initial steps involve securing the most valuable assets (data) and the primary entry vector (identity).
-
Phase 1: Identity and Access Modernization: Mandate MFA organization-wide. Adopt a centralized IdP. Inventory all human and non-human identities. Move all critical applications to authenticate through the IdP.
-
Phase 2: Data Classification and Protection: Discover and classify all sensitive data (PII, IP, financial). Enforce encryption everywhere (at rest and in transit). Implement DLP policies on key data repositories.
B. Segment and Enforce Access
Next, shift the network from implicitly trusting to explicitly verifying.
-
Phase 3: ZT Network Access (ZTNA) Adoption: Replace traditional perimeter VPNs with ZTNA solutions. This provides external users with direct, verified, least-privilege access to specific applications, rather than the entire internal network.
-
Phase 4: Micro-Segmentation Rollout: Begin segmenting the internal network, focusing first on high-risk, high-value assets (e.g., the Finance server farm, the R&D database). Use network policies to enforce communication only between authorized application services.
C. Optimize and Automate
The final phases focus on continuous validation and operational efficiency.
-
Phase 5: Device Health and Visibility: Implement EDR and MDM solutions to continuously assess and report device health. Integrate device health status into the Policy Engine’s trust algorithm.
-
Phase 6: Automation and Orchestration: Integrate the Policy Engine with XDR/SIEM tools. Create automated workflows (SOAR) to respond to anomalies and enforce policy dynamically (e.g., automatically revoking a credential if suspicious activity is detected).
5. Zero Trust in the Cloud Ecosystem
The cloud environment is ideally suited for Zero Trust implementation because cloud providers offer natively integrated services for IAM, encryption, and network control.
A. Cloud IAM as the Policy Engine
Cloud providers’ Identity and Access Management (IAM) systems (e.g., AWS IAM, Azure Active Directory) form the backbone of the ZTA Policy Engine.
-
Resource-Level Policies: Cloud IAM allows defining policies at the resource level (e.g., “Allow this specific service role to only write to this one database table”), which is fundamental to least privilege access.
-
Integrated Authentication: Cloud services inherently use these IAM roles and temporary credentials for service-to-service communication, natively supporting the “never trust” mandate for non-human identities.
B. Cloud Micro-Segmentation
Cloud networking primitives offer robust tools for micro-segmentation.
-
Security Groups: In cloud IaaS environments, Security Groups (or Network Security Groups) act as stateful, instance-level firewalls. By restricting traffic between instances to only the necessary ports and source/destination security groups, they enforce micro-segmentation.
-
VPC Network Policies: For containerized environments (Kubernetes), cloud-native network policies allow fine-grained, identity-aware segmentation between individual pods and services.
C. Data Encryption and Key Management
Cloud Key Management Services (KMS) provide the centralized, hardware-backed control over encryption keys required by ZTA.
-
Auditability: KMS automatically logs every action taken against a key, providing the continuous visibility required to audit and verify that data access policies are being followed.
Conclusion: The Foundation of Future Security

The Zero Trust Architecture is the inevitable and necessary evolution of enterprise security. It moves beyond the failed perimeter model to adopt a security strategy fit for the distributed, dynamic, and cloud-centric world. By adhering to the principle of “never trust, always verify,” ZTA ensures that access is meticulously granted based on identity, device posture, and context, limiting the damage an attacker can inflict if they gain a foothold.
Implementing Zero Trust requires commitment across seven pillars—from securing Identity and Devices to implementing continuous Visibility and Automation. It is a journey of modernizing infrastructure, centralizing policy, and continuously reducing implicit trust. The successful adoption of ZTA transforms security from a reactive barrier into an active, intelligent, and flexible enforcer of business policy, ensuring the resilience and integrity of the organization’s most valuable assets. Zero Trust is the only trust model that makes sense in the cloud.